Passwords are the digital keys to our lives. They unlock everything from our most sensitive financial data to our personal communications and cherished memories. For online businesses, they are a safety net that allows customers to transact business and make purchases with apparent security. Yet, for all their importance, passwords remain a glaring weak point in online security.
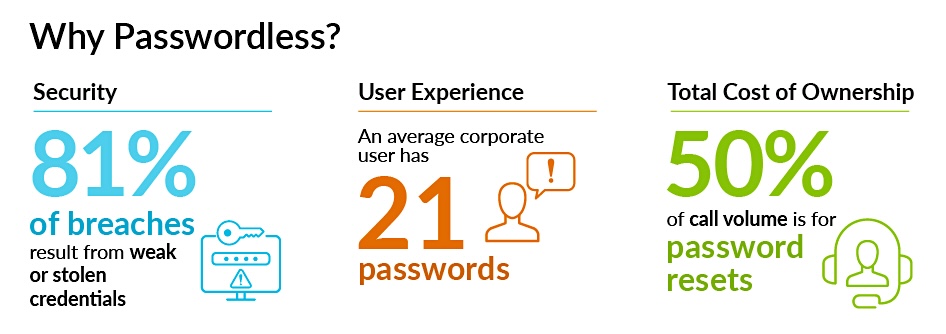
Consider this: 81% of data breaches hinge on compromised passwords. These breaches translate into real-world consequences like identity theft, financial fraud, account takeover, and ransomware attacks. The simple truth is that passwords, despite their ubiquity, are often weak, reused across platforms, and ripe for exploitation by cybercriminals.
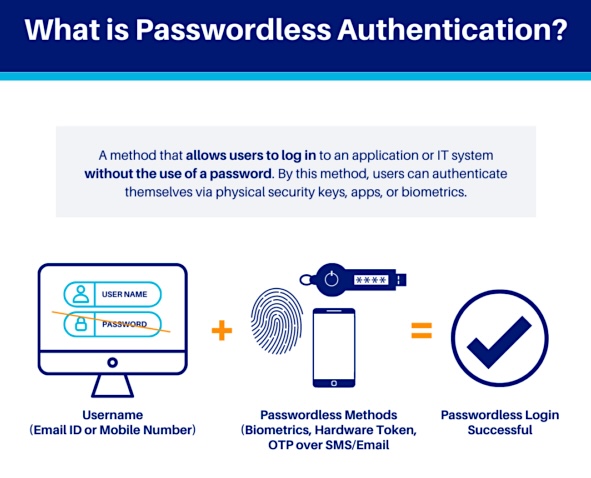
One of the solutions is a fundamental shift from traditional password-based security to passwordless authentication. Going passwordless offers a robust alternative and empowers you with a more convenient way to verify your identity. It eliminates the need for complex character strings and replaces them with more secure yet user-friendly methods, putting you in control of your digital experiences.
The Technology Behind Passwordless Authentication
Passwordless authentication is a paradigm shift in how we verify digital identities. It replaces the traditional ‘something you know ‘ factor (passwords) with ‘something you have’ (a device or token) or ‘something you are’ (biometric data). This shift is made possible by using unique cryptographic key pairs and advanced algorithms.
Public Key Cryptography
Public Key Cryptography (PKI) is a core technology in many passwordless systems, particularly those involving security keys or certain magic link implementations. Each user possesses a unique cryptographic key pair: a public key (shared with the service provider) and a private key (kept secret on the user’s device or in a secure enclave).
During registration, the user’s public key is registered with the service. When the user attempts to authenticate, a “challenge”, such as a randomly generated sequence that requires a response only an authorized entity can provide, is sent to their device. The user’s device signs this challenge using the private key and sends the response back to the service. The service then uses the user’s public key to verify the signature, thus authenticating the user without needing a password.
Protocols Used in Passwordless Authentication
Several protocols and standards can be integrated into a passwordless authentication ecosystem, though not all are exclusively for use in passwordless systems. These include, among others:
- FIDO2 – An open standard specifically designed to enable passwordless logins across devices and platforms, often using specialized hardware authenticators or built-in biometric sensors.
- SAML – This XML-based standard is used primarily to exchange authentication and authorization data. However, it can be configured to work with passwordless methods within a broader single sign-on (SSO) strategy.
- OAuth 2.0 – While mainly an authorization framework, OAuth can be part of a passwordless flow when combined with other protocols, especially for ‘Log in with [Provider]’ scenarios, in which users can leverage their existing accounts with providers like Google or Facebook to authenticate on other platforms.
8 Benefits of Passwordless Authentication
Passwordless authentication is not just a security measure but a strategic approach that enhances customer security, streamlines operations, reduces IT overhead and improves user experience. It’s a win-win for both security and efficiency.
Here are some benefits of the passwordless approach:
- Eliminates Password Vulnerabilities — By removing passwords, passwordless authentication drastically reduces the risks of password-seeking cyber attacks, such as phishing, credential stuffing, and brute-force attacks.
- Strengthens Authentication — Utilizing “something you have” (like a security key or mobile device) and “something you are” (biometrics) is inherently more secure than relying solely on “something you know” (a password).
- Thwarts Social Engineering — the passwordless approach helps prevent social engineering attacks, which manipulate users into revealing passwords, as there are no passwords to exploit. It aligns with the Zero Trust Architecture principles, minimizing implicit trust and verifying access continuously.
- Reduces IT Overhead — Eliminating the need for password resets, a typical IT burden, frees up valuable time and resources for strategic tasks.
- Streamlines Onboarding — Passwordless authentication accelerates user onboarding, which is particularly beneficial for organizations with high turnover or numerous customers.
- Improves User Experience — A frictionless login experience reduces user frustration, boosting engagement, productivity, customer satisfaction, and brand loyalty.
- Ensures Compliance — Passwordless authentication helps organizations adhere to regulatory requirements like GDPR and PCI DSS, demonstrating a commitment to data protection.
- Limits the Exposure of Credentials — as there are no passwords to be stolen.
What are the most common passwordless authentication methods?
Each passwordless authentication method offers a unique approach to verifying user identity, leveraging different technologies and protocols. The most common methods include:
1. Biometrics for Unique Identification
Biometric authentication hinges on the distinctive physiological or behavioral traits of individuals and uses the following techniques:
- Fingerprint Recognition: Advanced algorithms analyze minutiae points (ridge endings and bifurcations) to create a unique fingerprint template. Comparison algorithms then verify the live fingerprint scan against the stored template.
- Facial Recognition: Computer vision technologies and ML-based methods analyze facial landmarks, distances, and proportions. Algorithms like Eigenfaces and Fisherfaces, and similar deep learning models, extract features and match them against stored templates. Liveness detection techniques like blink detection or challenge-response tests prevent spoofing with photos or videos.
- Iris Scanning: Infrared cameras capture the complex patterns of the eye’s iris. Image processing algorithms extract features like furrows, ridges, and crypts, creating an iris code. Matching algorithms compare the iris code against stored templates with high accuracy.
- Voice Recognition: Vocal characteristics like pitch, frequency, and formants are analyzed. Then, machine learning methods like Gaussian Mixture Models (GMMs) or algorithms like Deep Neural Networks (DNNs) create voiceprints and match them against stored samples.
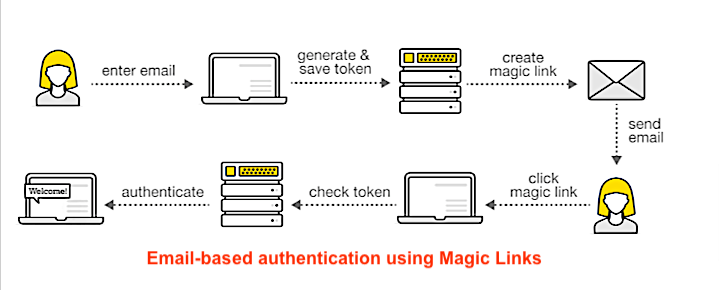
2. Magic Links for Cryptographically-secure Email Authentication
Magic links, also known as email magic links, work by generating a unique, one-time-use link that contains a token – then sending it to the user’s email address, phone number, or other messaging platform. This method relies on the security of the user’s email account and the cryptographic strength of the link itself.
First, a unique, time-limited link is generated using a cryptographic hash function (such as SHA-256), and applied to a combination of user-specific data and a random nonce (an arbitrary number that can be used just once in a cryptographic communication). This ensures the link’s unpredictability and prevents tampering.
Next, the link is sent to the user’s email (or other platform) for authentication. Upon clicking, the server verifies the link’s integrity and expiration time. If valid, the user is authenticated and logged in.
3. One-Time Passcodes (OTPs) with Algorithmic Code Generation
OTPs are generated using algorithms like the Time-based One-time Password Algorithm (TOTP) or the HMAC-based One-time Password Algorithm (HOTP). Here’s how each works:
- TOTP generates a code based on a shared secret key and the current time. The server and the user’s device calculate the same code, ensuring synchronization and validity for a short period.
- HOTP generates a code based on a shared secret key and an incrementing counter. The code remains valid until used, making it less time-sensitive than TOTP.
4. FIDO2 Security Keys for Public Key Cryptography in Action
FIDO2 security keys utilize public key cryptography and the WebAuthn standard to enable secure, passwordless logins.
The user’s device generates a public-private key pair in the registration stage. The public key is registered with the service, while the private key remains on the security key or the user’s device.
Next, the service sends a challenge to the user’s device for authentication. Using the private key, the security key signs the challenge and then sends the response back to the service. The service verifies the signature using the stored public key, authenticating the user.
5. Push Notifications for Mobile-Driven Authentication
Push notifications for authentication also rely on public key cryptography. First, the user’s mobile device generates a key pair, and the public key is registered with the service. Then, the service sends a challenge to the user’s device via a push notification. The device’s private key signs the challenge, and the signed response is returned for verification.
Key Challenges and Pitfalls of Passwordless Authentication
Despite the security enhancements offered by passwordless authentication, technical vulnerabilities exist within each method, requiring careful consideration and mitigation strategies.
Biometric Spoofing and Liveness Detection
Biometric spoofing remains a concern, with sophisticated techniques like 3D mask creation and deepfake technology posing threats to facial recognition systems. Fingerprint spoofing, through artificial replicas or lifted latent prints, also challenges authentication accuracy. Voice recognition systems are vulnerable to voice synthesis and replay attacks. Mitigating these risks necessitates employing multi-modal biometrics, liveness detection techniques, and/or continuously updating algorithms to avoid evolving spoofing techniques.
Code and Link Interception
Another vulnerability is the interception of codes and links during transmission. Man-in-the-middle attacks can intercept OTPs or redirect magic links, while SIM-swapping attacks grant attackers access to SMS-based OTPs.
Phishing scams can trick users into revealing codes or clicking on malicious links. Encrypted communication channels, DMARC implementation, and user education are crucial countermeasures.
Security Key Vulnerabilities
While generally secure, FIDO2 security keys face risks related to physical theft, loss, supply chain compromise, session hijacking, and DNS cache poisoning. These keys are essential to digital asset protection, particularly in enterprise environments. Implementing 2FA with a PIN or biometric, enabling remote key disabling, and sourcing from reputable vendors mitigate these risks.
Device Compromise
Push notifications are susceptible to device compromise and may present usability challenges for users with limited connectivity. Device security measures, strong encryption, and alternative authentication methods address these concerns.
Understanding these vulnerabilities allows organizations to implement appropriate security measures and leverage solutions like Memcyco, which inherently includes algorithms that combat the principal vulnerabilities of passwordless authentication.
9 Steps to Implement Passwordless Authentication
A successful transition to passwordless authentication involves the following nine steps:
1. Scoping
Identify target applications and systems, prioritizing critical ones. Analyze existing infrastructure for integration points and areas needing upgrades.
2. User Choice
Provide users with options for passwordless methods, allowing them to choose the authentication factor(s) that best suit their preferences and specific use cases.
3. Selecting Methods
Choose passwordless options based on organizational needs, security requirements, and user preferences. Consider factors like data sensitivity, user technical capabilities, and desired convenience. Key options include:
- Biometrics: Suitable for high-security, convenience-focused scenarios requiring robust liveness detection and privacy compliance.
- FIDO2 Keys: Offers strong phishing resistance but needs secure key management.
- Magic Links/OTPs: Convenient alternatives requiring secure delivery and short validity.
- Push Notifications: Leverages mobile devices but must prioritize encryption and device binding.
4. Pilot Program
Test and refine implementation with a limited user group, gathering feedback and monitoring performance metrics.
5. Integration
Using vendor-provided APIs and SDKs, ensure seamless integration with existing IAM systems, SSO solutions, and other infrastructure.
6. Security Policies
Develop comprehensive policies defining roles, responsibilities, incident response, and access revocation procedures.
7. User Education
Provide comprehensive training and resources, explaining benefits, usage, security considerations, and troubleshooting steps. Education should also include awareness of generative AI security standards, especially with AI playing a growing role in authentication processes.
8. Gradual Rollout
Gradually expand access, starting with low-risk applications and users, monitoring performance closely.
9. Continuous Monitoring
Implement robust monitoring to track authentication logs, detect anomalies, and adapt strategies based on emerging threats and user needs.
Memcyco: Fortifying Passwordless Authentication
With its diverse array of methods and robust security benefits, passwordless authentication ensures greater security in digital identity verification. While challenges exist, proactive mitigation strategies help create a transition to a safer, passwordless future. Understanding the intricacies of the many options for passwordless authentication allows organizations to choose solutions tailored to their specific needs.
As detailed earlier in this post, passwordless authentication still has its issues. Many are unaware that ‘passwordless’ passkeys still rely on regular passwords being inputted by customers whenever a device connects to any web application for the first time. This step is repeated whenever a device is lost, broken, or replaced, allowing fraudsters to imitate account issues, duping customers into inputting passwords into impersonated websites—and leaving the door open for Account Takeover (ATO) attacks.
That’s why it’s advisable to bolster your passwordless authentication solution with Memcyco’s Digital Impersonation Protector (DIP) product, which inherently includes algorithms that combat the main vulnerabilities of passwordless authentication. DIP focuses on combating website impersonation scams, but as part of its arsenal of tools also provides a fortification layer on top of passwordless authentication methods, to ensure extra robustness when implementing these methods as part of a company’s broader cybersecurity strategy.
Book a demo with Memcyco to learn how we provide customer security beyond passwordless authentication.